
The Internet Protocol (IP) is the most common computer communication protocol today. It is the base protocol used for Internet, e-mail and almost every newly installed network.
One of the reasons for its popularity is its scalability. In other words, it works as well in very small installations as it does in very large ones and is supported by an increasingly wide range of high performance, low-cost and industry-proven equipment and technologies.
Ethernet
In today's offices, computers are most likely to use TCP/IP and are connected via an Ethernet network, either in a wired LAN (local area network), or in a wireless LAN. Ethernet gives a fast network at a reasonable cost. Most modern computers are supplied with an integrated Ethernet interface or can easily accommodate an Ethernet connection card.
Common Ethernet types
10 Mbps Ethernet
This standard is rarely used in production networks today due to its low capacity, and has been replaced by 100 Mbit Ethernet since the late '90s. The most common topology used for 10 Mbit Ethernet was called 10BASE-T; it uses four wires (two twisted pairs) on a Cat-3 or Cat-5 cable. A hub or switch sits in the centre and has a port for each node. The same configuration is used for Fast Ethernet and Gigabit Ethernet.
Fast Ethernet (100 Mbps)
Supporting data transfer rates of up to 100 Mbps, Fast Ethernet is the most common Ethernet type used in computer networks today. The main standard is called 100BASE-T. Although newer and faster than 10 Mbit Ethernet, in all other respects it is the same. The 100BASE-T standard can be subdivided into:
* 100BASE-TX: Uses twisted pair copper cabling (Cat-5).
* 100BASE-FX: 100 Mbps Ethernet over optical fibre.
Note: most 100 Mbit network switches support both 10 and 100 Mbit to ensure backward compatibility (commonly called 10/100 Network switch).
Gigabit Ethernet (1000 Mbps)
This is the current standard that is being endorsed for desktop computers by networking equipment vendors. The most common use today is however for backbones in between network servers and network switches. 1000BASE-T is widely used and it can be subdivided into:
* 1000BASE-T: 1 Gbps over Cat-5e or Cat-6 copper cabling.
* 1000BASE-SX: 1 Gbps over multimode fibre (up to 550 m).
* 1000BASE-LX: 1 Gbps over multimode fibre (up to 550 m). Optimised for longer distances (up to 10 km) over single-mode fibre.
* 1000BASE-LH: 1 Gbps over single-mode fibre (up to 100 km). A long-distance solution.
10 Gigabit Ethernet (10 000 Mp/s)
This is viewed as the new choice for backbone in enterprise networks. The 10 Gigabit Ethernet standard uses seven different media types for LAN, WAN and MAN (metropolitan area network). It is currently specified by a supplementary standard, IEEE 802.3ae, and will be incorporated into a future revision of the IEEE 802.3 standard.

A variety of network types are available today. 100 Mbit networks are more than enough for a network camera, while Gigabit is appropriate for backbones.
Power over Ethernet
Power over Ethernet (also referred to as PoE or power over LAN) is a technology that integrates power into a standard LAN infrastructure. It enables power to be provided to the network device, such as an IP phone or a network camera, using the same cable as that used for network connection.
Power over Ethernet is especially suited for IP-Surveillance and remote monitoring applications because it eliminates the need for a power outlet at the camera location - particularly in places previously thought of as impractical or too expensive to connect to a power outlet. This makes installation easier and cheaper since there is no need for separate power and data cable infrastructure and costly AC outlets. In addition, an electrician does not need to be involved.
Another benefit of power over Ethernet is the UPS function. Many companies have their network switches connected to a UPS (uninterrupted power supply) device. Since the power over Ethernet hubs are connected to the network switches, the cameras and video servers can continue to function even in the case of a power shortage.
PoE technology is regulated in a standard called IEEE 802.3af and is designed in a way that does not degrade the network data communication performance or decrease the network reach. The power delivered over the LAN infrastructure is automatically activated when a compatible terminal is identified, and blocked to legacy devices that are not compatible. This feature allows users to freely and safely mix legacy and PoE-compatible devices, on their network.
The standard provides power up to 15,4 W on the switch or midspan side, which translates to a maximum power consumption of 12,9 W on the device/camera side - making it suitable for indoor cameras. Outdoor cameras as well as PTZ and dome cameras normally have a power consumption that exceeds this, making PoE functionality less suitable. Some manufacturers also offer non-standard proprietary products providing suitable power for these applications as well, but it should be noted that since these are non-standard products, no interoperability between different brands is possible. The 802.3af standard also provides support for so-called power classification, which allows for a negotiation of power consumption between the PoE unit and the devices. This means an intelligent switch can reserve sufficient, and not superfluous, power for the device (camera) - with the possible result that the switch could enable more PoE outputs.
Wireless network technology
Even if wired networks are present in most buildings today, sometimes a non-wired solution holds substantial value to the user, financially as well as functionally.
For example, it could be useful in a building where the installation of cables would not be possible without damaging the interior, or within a facility such as retail outlet where there is a need to move the camera to new locations on a regular basis without having to pull new cables every time.
Another common use of wireless technology is to bridge two buildings or sites together without the need for expensive and complex ground works.
There are two major categories for wireless communications:
* Wireless LAN (also known as WLAN):
A LAN is by definition a local area network, ie, over short distances and normally indoors. Nowadays, the wireless LAN standards are well defined and devices from different vendors work well together.
* Wireless bridges:
When it is necessary to connect buildings or sites with high speed links, a point-to-point data link capable of long distances and high speeds is required. Two commonly used technologies are microwave and laser.
Wireless LAN standards
802.11a
Standard using the 5 GHz band providing up to ~24 Mbps actual throughput at up to 30 m/100 feet in outdoor environments. Limited range of products supporting it. Theoretical bandwidth is 54 Mbps.
802.11b
The most commonly used standard, providing up to ~5 Mbps actual throughput at up to 100 m/300 feet in outdoor environments. It uses the 2,4 GHz band. Almost all products on the market support this standard. Theoretical bandwidth is 11 Mbps.
802.11g
Fairly new standard providing improved performance compared with 802.11b. Up to ~24 Mbps actual throughput at up to 100 m/300 feet in outdoor environments. It uses the 2,4 GHz band. Theoretical bandwidth is 54 Mbps.
Typical network including both wireless and wired connections:
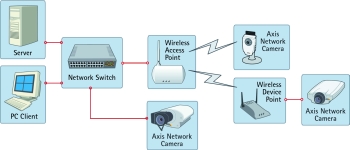
This diagram illustrates a common use of wireless technologies:
* The centre point here is the network switch. To the left, a server (top) and a PC client (bottom), are connected using wired Ethernet. Next to the switch, there is a wireless access point. This device manages all the wireless devices within range.
* Two wireless devices are represented on this diagram:
* Camera with built-in support for wireless communications.
* A wireless device point. This device provides wireless communication and connects directly to an Axis network camera that has no built-in support for wireless communications.
It is also possible to connect the server and the PC wirelessly. But as the wireless network bandwidth is limited compared with the wired one, the goal should always be to use wired networks whenever possible.
About security in wireless networks
Due to the nature of wireless communications, everyone with a wireless device present within the area covered by the network will be able to participate in the network and use shared services; hence the need for security. The most commonly used standard today is WEP (wireless equivalent privacy), which adds RSA RC4-based encryption to the communication, and prevents people without the correct key to access the network. But as the key itself is not encrypted, it is possible to 'pick the lock', so this should be seen only as a basic level of security. A WEP key is normally of either 40 (64) bits or 128 bits in length. Lately, new standards being deployed significantly increase security, such as the WPA (WiFi protected access) standard, which takes care of some shortcomings in the WEP standard, including the addition of an encrypted key.
Wireless bridges
Some solutions may also use other standards than the dominating 802.11 standard, providing increased performance and much longer distances in combination with very high security. This also includes the use of other means of radio frequency, such as microwave links.
Another common technology are optical systems such as laser links. A microwave link can provide up to 1000 Mbps for distances up to 130 km. For locations outside the range of all these systems, there is also the option of satellite communication. Due to the way this system operates, transmitting up to a satellite and back down to earth, the latency can be very long (up to several seconds). This makes it less suitable for functions like manual dome control and video conferencing where low latency is preferred. If larger bandwidth is required, the use of satellite systems also becomes very costly.
Data transport methods
IP addresses
Each device on a LAN (local area network) must have a unique address. This is commonly called the 'IP address', and is occasionally referred to as the Ethernet address. An IP address consists of four numbers separated by a dot '.', each number is in the range 0-255. For example, the address could be '192.36.253.80'. The first three groups of digits will be common to all devices connected to the same segment, which means that all units within the same segment will have a common address beginning with 192.36.253.
Data transport protocols for network video
The most common protocol for transmitting data on computer networks today is the TCP/IP Protocol suite. TCP/IP acts as a 'carrier' for many other protocols; a good example is HTTP (Hyper Text Transfer Protocol), which is used to browse Web pages on servers around the world using the Internet.
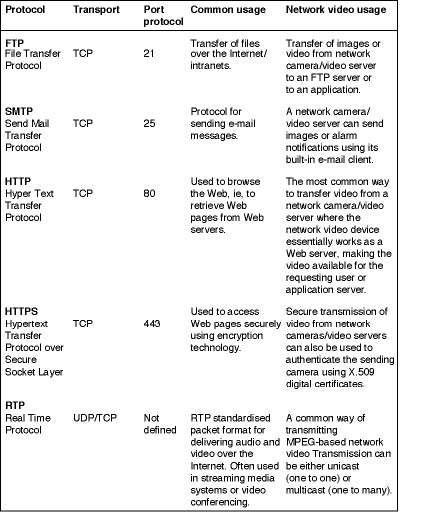
IP uses two transport protocols: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP provides a reliable, connection-based transmission channel; it handles the process of breaking large chunks of data into smaller packets, suitable for the physical network being used, and ensures that data sent from one end is received on the other. UDP, on the other hand, is a connectionless protocol and does not guarantee the delivery of data sent, thus leaving the whole control mechanism and error-checking to the application itself.
Network security
There are several ways to provide security within a network and between different networks and clients. Everything from the data sent over the network to the actual use and accessibility of the network can be controlled and secured.
Secure transmission
Providing secure transmission of data is similar to using a courier to bring a valuable and sensitive document from one person to another. When the courier arrives at the sender, he would normally be asked to prove his identity. Once this is done, the sender would decide if the courier is the one he claims to be, and if he can be trusted. If everything seems to be correct, the locked and sealed briefcase would be handed over to the courier, and he would deliver it to the recipient. At the receiver's end, the same identification procedure would take place, and the seal would be verified as 'unbroken'. Once the courier is gone, the receiver would unlock the briefcase and take out the document to read it.
A secure communication is created in the same way, and is divided into three different steps:
* Authentication.
* Authorisation.
* Privacy.
Authentication
Authentication means verifying that a device is what it claims to be. The initial step is for the user or device to identify itself to the network and the remote end. This is done by providing some kind of identity to the network/system, like a username and password or an X509 (SSL) certificate. The provided identity is then verified, for example by matching the username and password against information in a database of approved identities.
Authorisation
Authorisation means granting users access rights to resources. This second step is to find out if the authenticated user is permitted to use the system. A user can belong to a group that only has permission to view the data. Another user can be an administrator and has the permission to configure the system.
Privacy
The final step is to apply the level of privacy required. This is done by encrypting the communication, which prevents others from using/reading the data. The use of encryption could substantially decrease performance, depending on the implementation and encryption used.
Privacy can be achieved in several ways. Two commonly used methods are:
* VPN (virtual private network).
* HTTP over SSL/TLS (also known as HTTPS).
VPN (virtual private network)
* A VPN creates a secure tunnel between the points within the VPN. Only devices with the correct 'key' will be able to work within the VPN. Network devices between the client and the server will not be able to access or view the data. With a VPN, different sites can be connected together over the Internet in a safe and secure way.
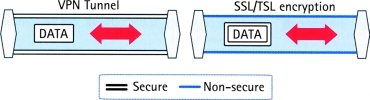
HTTP over SSL/TLS
Another way to accomplish security is to apply encryption to the application data itself. In this case, there is no secure tunnel as with the VPN solution, but the actual application data sent is secured. There are several different encryption protocols available, for example SSL/TLS. When using HTTP over SSL/TLS, the device or computer will install a certificate into the unit, which can be issued locally by the user or by a third-party such as Verisign. In most cases when a connection between two devices is established, the certificate of the server will be verified by the client and, if trusted, an encrypted communication is opened. When creating a secure connection to Websites such as Internet banks, the certificates of the two units will be verified. When you see 'https://...' in the Web address, the 's' stands for secure and it means that you are requesting a secure connection.
Protecting single devices
Security also means protecting single devices against intrusions, such as unauthorised users trying to gain access to the unit, or viruses and similar unwanted items.
Access to PCs or other servers can be secured with user names and passwords, which should be at least six characters long (the longer the better), combining numbers and figures (mixing lower and upper cases). In the case of a PC, tools like finger scanners and smartcards can also be used to increase security and speed up the login process.
To secure a device against viruses, worms and other unwanted items, a virus scanner of good quality with up-to-date filters is recommended. This should be installed on all computers. Operating systems should be regularly updated with service packs and fixes from the manufacturer.
When connecting a LAN to the Internet, it is important to use a firewall. This serves as a gatekeeper, blocking or restricting traffic to and from the Internet. It can also be used to filter information passing the firewall or to restrict access to certain remote sites.
Ethernet network components and their relative protocols
Hubs, switches and routers
Hubs are essentially used as connection boxes to allow several pieces of equipment to share a single Ethernet connection. Usually 5-24 devices can be connected to one hub. If more devices are used, another hub can be added. One hub can be directly connected to no more than four other hubs in a row for effective communications. A hub forwards all data packets to everything connected on the network, even to unintended destinations. Instead of hubs, switches are more commonly used today.
A switch is an equipment that allows different computers or devices on a network to communicate directly with one another in a smooth and efficient manner. A switch forwards data packets to only the intended computer(s). It can transmit data packets from different sources simultaneously. Although it is somewhat more expensive than a normal hub, a switch offers much greater capacity and is generally recommended. Switches can interface between 10, 100 and 1000 Mbps.
A switch may also include the function of the router, a device or program that can determine the route, and specifically, what adjacent network point the data should be sent to.
For instance, you want to record images from six network cameras connected to a server placed in a room 100 m away. Instead of using cables from each camera with 100 m of cables (600 m cables in total), you could use a hub or a switch, which interconnects the cameras and only need one 100 m cable over a 100 Mbps Ethernet network. The cable used for these kinds of connections, FTP twisted pair cabling or UTP unshielded twisted pair, is also cheaper than the coax cable used in analog installations. And since the installation using a switch requires less cabling, the overall cost will be kept to a minimum. This is a huge advantage for IP network video systems compared with analog technology.
A router is used to connect networks together. It is also used to connect networks to the Internet. A router selectively forwards network packets according to their IP address, ensuring that information goes only to its intended destination(s) and not to where it is not needed. A router can determine the route, and specifically, what adjacent network point the data should be sent to. A router plays an important role in keeping large volumes of data from clogging the connections of 'innocent bystanders' and slowing down the network. Many routers have built-in firewalls and can keep a record of Internet activity on the network. Routers may also mask the identities of the computers they serve and may give you greater control over what type of data can leave or reach your network.
Example:
If many devices are connected to the same network, the network should be divided into segments with switches or routers placed in between.
For instance, an airport with two buildings using 170 cameras each needs to be connected to the same security central several kilometres away. To have access to all cameras simultaneously, you simply divide the cameras into two networks and connect them together with a switch or router.
To enhance the speed of a network and enable greater simultaneous data transfers, you can use a combination of switches and routers with different capacities (speed).
IP addresses
To be able to connect directly to the Internet, each device on a LAN (local area network) must have a unique address, commonly called the 'IP address'.
An IP address consists of four numbers separated by a dot '.'; each number is in the range 0-255. For example, the address could be 192.36.253.80. The first three groups of digits will be common to all devices connected to the same segment, ie, in the previous example, all units within the same segment will have a common address beginning with 192.36.253. Each IP address is divided into 65,535 ports. Different applications use different IP ports. The Internet browser (HTTP) on a computer uses port number 80 to receive and view Web pages (eg 192.36.253.80:80). Port 80 is the standard port that Axis network cameras use to send live video. An e-mail program uses port number 25 to send e-mail and port number 110 to receive e-mail from the e-mail server. Normally users do not need to concern themselves with port numbers.
Data packets
All data is sent within a data packet, and all packets are labelled with the address of the destination. In an Ethernet network, a packet is transmitted approximately every 0,1 milliseconds. This means that up to 10 000 packets can be transmitted every second. Today's computers and network devices have a high capacity to simultaneously communicate with several different units. A modern network camera can send images to at least five computers simultaneously. With a network camera sending images to an external application server, instead of directly to the viewers, realtime video can be seen by an unlimited number of viewers.
NAT routers
All devices connecting directly to the Internet must have a unique public IP address. Public IP addresses are sold by Internet Service Providers (ISPs). A device called a network address translator, NAT, can separate a LAN net from the Internet. A NAT can either be a small box or a program running on a computer. Most office LANs are normally connected to the Internet to make it possible to send e-mails and to browse the Internet.
Gateways
Gateways provide a convenient way to create a local network. A gateway works as a combined router, switch and NAT and is available from many manufacturers.
DHCP servers
It takes time to administer the IP addresses for large numbers of devices on a network. To reduce this administration time and keep the number of IP addresses to a minimum, you can use a device called a DHCP server. This type of server automatically issues network devices with IP addresses when they connect to the network.
Domain name servers
In larger networks a domain name server (DNS) is included. This is literally a 'name' server; it associates and remembers given names to corresponding IP addresses. For example, a network camera monitoring a door is more easily remembered and accessed by the word 'door' than it is by its IP address, eg, 192.36.253.80.
Firewalls
All networks connecting to the Internet should be protected against hackers. An Internet 'firewall' is a device that ensures that only authorised users can access devices connected to the LAN. In larger networks, it is common to use a PC to perform the combined functions of a NAT, DHCP server and firewall. This PC may also be used as an e-mail server, name server and image storage.
Source: Axis Communications' Technical Guide to Network Video.
For more information contact Roy Alves, Axis Communications SA, +27 (0) 11 548 6780, [email protected], www.axis.com
© Technews Publishing (Pty) Ltd. | All Rights Reserved.