
Hand vascular pattern person identification technology is the next-generation in biometric technology. The world biometrics market is growing at more than 30% every year due to the rising need to protect valuable resources from increased risk of terrorism, crime and violence.
The challenge to achieve higher profits in the business world has created a critical need for more effective management of valuable human resources. Many entities such as governmental organisations, financial industries, hospitals, Internet societies and transportation authorities are demanding technology to meet these needs.
The DexID Vein Scanner (VP-II) system verifies human users by utilising a state-of-the-art recognition algorithm based on the hand vascular pattern extracted by an infrared optical sensor system. Vein pattern and heat differential patterns are used in combination to form a unique template. The vascular pattern of each individual is unique and more accurate (99,98%) than standard fingerprint biometric practices.
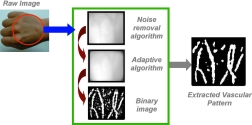
The vein scanner works at a speed of 0,4 seconds to verify the person or to allow or deny access and an accuracy level of 99,98%.
The system is believed to change the paradigm of the biometric system market through its system usability. Expert market research shows the lack of system usability as a major technical obstacle preventing market dissemination of biometric technology.
According to Jans Wessels, managing director of Dex Group informatix, a biometric system should:
* Be usable to a whole population (user group). Usability is defined as the percentage of unspecified adult population that is capable of using a biometric system. Based on the world's biometric system market analysis, the most critical obstacle in biometrics dissemination has been the lack of system usability. Average usability of fingerprint-based system is known to be about 95% because of absence or weakness of their fingerprints. About 2% of persons do not have proper fingerprints, and many people who use their hands intensively for work struggle to enroll their fingerprints. For this reason, fingerprint-based biometric systems usually provide a backdoor such as a key or numeric password. Once a biometric system has a backdoor, it is no longer a biometric system.
* Not leave a trace of residual features after use. If a biometric system leaves residual features from physical contact, the features could be easily duplicated for forgery. When a biometric device requires physical contact from users (for example, fingerprint scanner or hand geometry system), a counterfeit bio-feature could be easily re-constructed. Then the device is insecure.
* Reject non-human features from enrolment. Non-human features should not be allowed to enrol if the system is a true biometric system.
* Keep a secure database of the personal biometric features. VP-II systems store users' vascular data in hardware after encryption. The ability to hack into systems which store biometric data makes the entire system insecure.
According to Wessels standard software is available that controls use of VP-II. This enables administration of users, logs system user access records, and reports system activities. NetControl works with both standalone VP-II and VP networks. NetControl runs on all Microsoft Windows Platforms. NetControl provides an easy-to-use graphical method to set up or modify network configuration, automatic system diagnosis, and flexible user-management methods.
Exporting of logs allows quick and easy integration to various third-party solutions such as time and attendance, basic physical access control or scheduling systems.
For value added resellers or distributors, VP-II SDK is provided for quick and easy application development. Utilising SDK, application developers need not worry about hardware details of VP-II technology. In addition, a complete set of sample codes enables developers to build an application in a very short period. VP-II SDK consists of following components: VPX (a set of DLLs to control hardware and communication), sample code and on-line developer's reference documentation. VP-II SDK supports all Windows platforms.
South Africa presents very unique challenges with respect to the diversity and wide application areas of the workforce, where positive identification of people is required. High crime in South Africa further seems to promote bypassing of time and attendance systems. High volume use makes conventional card systems particularly vulnerable.
Due to usability DexID VP-II is ideally positioned for use in the security of the mining, construction and chemical industries. The use of vein patterns removes the negative perceptions linked to fingerprint systems that are commonly used by police and governments for criminal purposes.
Initial tests have proven highly successful with various skin types and hand sizes in the local environments. Humidity and heat factors have also not presented any problems during initial testing. With no contact to sensing area, maintenance is limited and allows rollout in areas where hands contain grime and grit without affecting performance. Infrared scan removes impact of dirt and scars on skin.
Currently, over 5000 of the units have been installed internationally. The sites range from banks (Sumitomo Mitsui Banking Corporation, Asahi Banking System, Kookmin Bank, Industrial Bank of Korea) using them for general access control to secure areas, access to safety deposit boxes for banking clients and access to vaults, police stations (Tokyo Metropolitan Police, National Police Agency of Korea), casinos, apartment buildings (Yokohama mansion), defence departments (Ministry of National Defense, Korea), airports (Toronto Pearson International Airport), dormitories (KakiBukit Dormitory), hospitals (Sendai Hospital), corporations (LG Development, Internet Security Systems K.K.) and universities (Changwon National University).
DexSecurity Solutions, a local designer and manufacturer of biometric security systems for access control and time and attendance records, has acquired the sole right to import the Techsphere VP-II security system. In terms of the contract, Dex will handle the distribution of the infrared vein structure biometric scanners in South Africa and the entire sub-Saharan continent.
In conclusion, the VP-II will become the ultimate high performance, affordable biometric system.
Technology introduction
* VP-II Technology provides the ultimate system usability of 99,98% - this means that only one in 5000 persons might find it more difficult to enrol compared to one in a hundred persons for fingerprint systems!
* High performance but affordable biometric systems. The security level of VP-II products is high enough to compete with all other high-end biometrics systems. VP-II shows no performance degradation, even with scars or contamination of hand, or even in rugged environments such as construction sites, mines, army, factories etc. VP-II prevents enrolment of non-biometric patterns and fraudulent use of biometric features.
* The sensor requires no physical contact, so that it provides excellent convenience, sanitary use, and prevents copying system-residual biometric patterns.
* Network interface is possible via RS422, TCP/IP protocols, using UTP (Cat 5) cables and standard RJ45 connectors. RS485 is available for linking to local site controllers or RS232 for single PC connectivity. The system also has a multimode Wiegand Input/Output capability for integration to various card systems.
Specifications
Usability: 99,98%.
Verification speed: 0,4 sec/person.
Enrolment speed: 0,4 sec/person twice.
Security: FAR 0,0001%, FRR 0,1%.
Housing material: PC + ABS.
Power voltage: AC 85-260 V.
Operation temperature: -5 to 50°C.
Operation humidity: 10% to 90%.
Power consumption: DC 12 V, 2 A.
Dimensions: scanner 247 (L), 135 (W), 150 (H) mm; controller 140 (L), 170 (W), 37,5 (H) mm.
Benefits
* Speed, throughput and accuracy.
* Hygienic.
* No performance degradation in industrial environments.
* No performance degradation with substantial contamination of hands.
* No performance degradation over long periods of use.
* No physical contact of sensing area.
* Large scale features - high performance even with reasonably large scars and contamination.
* Usability.
* User perception and convenience.
* Ease of set-up and maintenance.
* System reliability.
* High performance in poor environment.
* High performance in network environment.
* High performance at affordable price.
For more information contact Jans Wessels, DexSecurity Solutions, 011 644 6500, [email protected]
© Technews Publishing (Pty) Ltd. | All Rights Reserved.