
Protection systems integrate people, procedures and equipment to safeguard assets against theft, sabotage and other malevolent attacks. Organisations typically have two major protection systems, one for physical security and one for IT security.
Physical security and IT security
Physical security focuses on the protection of physical assets, personnel and facility structures. This involves managing the flow of individuals and assets into, out of, and within a facility. IT security focuses on the protection of information resources, primarily computer and telephone systems and their data networks. This involves managing the flow of information into, out of, and within a facility's IT systems, including human access to information systems and their networks. Clearly these two are separate domains. Why should they be integrated?
A management issue
The question above accurately reflects the thoughts of most security practitioners as they approach this subject. How is the question misleading? To lean on a common idiom, it focuses on the trees rather than the forest.
No one is going to integrate a brick wall and a database. However, the management of who is allowed inside the wall and inside the database must be integrated, or there will be gaps in the organisation's security. Figure 1 below illustrates the concept of integrated security management. Whenever you hear or read the phrase 'integration of physical and IT security,' think 'integration of physical and IT security management' and you will be on the right track.
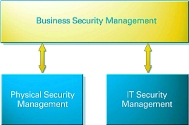
In almost every large enterprise, the physical and IT security departments operate independently of each other. They are generally unaware of the strengths and weaknesses of one another's practices, the liabilities of operating independently, and the benefits of integrated security management.
Integrating security management
Security objectives are carried out through the application of security policies, processes and procedures. Figure 2 below describes key security management processes and the physical and IT security processes and technologies that support them.

While it is true that many of the physical and IT security processes and procedures must be integrated at the technology level, it is not the technology that defines the integration. The business processes and procedures define it; the technology implements it. That is why the first step in integrating physical and IT security is an examination of security-related business requirements and the physical and IT security processes that support them. The integration of the business processes will determine where integration of physical security and IT technology is required.
In 'The Convergence of IT and Physical Security', an article written for Faulkner Information Services, a provider of in-depth information for technology professionals (www.faulkner.com), Laurie Aaron, director of business development for Tyco Safety Products' North American Sales Channels, says, "The lack of technical integration between physical security systems and IT security systems has resulted in organisational and procedural gaps for virtually every organisation in the world. Beside a few government agencies, very few organisations have adopted a comprehensive security strategy encompassing both physical and IT security. From an organisational standpoint, very few organisations have formal procedures in place between the different departments handling physical and IT security. Excessive risk exposure results from this lack of manageability."
If an organisation fails to examine its security procedures, gaps in protection are certain to occur. Usually the larger the company, the larger the security gaps, and the larger the opportunities for cost reduction.
Tatum Partners (www.tatumpartners.com) is the largest professional services provider of financial and information technology leadership in the United States. Tatum is a national organisation of 400 former chief financial, chief information and chief technology officers of world-class organisations such as the CIA, Nabisco, Hilton, Disney and IBM.
Joel Rakow, a Tatum partner located in the Los Angeles area, said, "We encourage every client, if they do nothing else, to integrate physical access controls with the corporate network. It lays the groundwork for a proactive security programme that enables early detection of emerging security attacks, and it produces immediate reduction of the cost of the security effort. Our Tatum CFOs calculate the return on investment to be between 16 and 18 months.
"We also like to point out that integrating physical and data security is a great mitigator against the legal liability of being found negligent in our client's 'duty to protect' sensitive information protected by such legislation as California Senate Bill 1386, Gramm-Leach-Bliley and HIPAA," said Rakow.
Benefits of centralised management
Managing users, their privileges and their credentials - a process called user provisioning - is one of the biggest challenges faced by organisations. Typically, HR makes the first database entry for a new user, in support of payroll and other employee-related functions. Security makes another entry, to provide an access control card/ID badge for physical access to facilities. IT makes a third entry, to provide access to information systems. The results of inconsistencies between the three areas range from personal inconvenience, such as an employee being denied access to parking or to the computer network, to significant corporate risk, such as failure to suspend physical or network access privileges immediately upon termination.
Such inconsistencies motivate people to bypass security by manually affording access (holding a door open) or sharing information system passwords. This often results in a person gaining access to areas and information to which he or she would not normally have access. These types of access violations are undocumented. Furthermore, not having centrally managed users means that the question 'Who has access to what?' cannot be answered quickly enough to provide ideal response times in the event of a suspected breach or a heightened security condition.
Reducing the user provisioning steps from three down to one not only eliminates the security vulnerabilities and enforces consistent role-based privileges across the entire organisation, but may drastically reduce the cost of managing users.
Challenges to integration
The sidebar titled 'Platforms Supporting Integration' presents three vendors of security management products that offer significant support for the integration of physical and IT security. Two of the product offerings are comprehensive physical security application suites, and one is a product specifically designed to integrate physical and IT security management. While several thousand customers currently use the two security application suites, few are currently integrating physical and network security. Why?
There are several distinct challenges that to date have hindered efforts to integrate physical and IT security, including the following:
* Initial focus on technology issues rather than security management issues.
* Conflicting or lacking standards.
* Apparent reluctance of physical security practitioners to embrace IT.
* No clear roadmap to organisational readiness.

© Technews Publishing (Pty) Ltd. | All Rights Reserved.