
South Africa is a country with exceptionally high crime rates, and petty crime in office buildings is no exception. Last year, as much as 63% of total reported security breaches were due to theft of IT equipment1. For security managers, this is an ongoing source of frustration. Larger objects (such as desktop PCs, for example) are fairly easy to spot, and subsequently difficult to steal. But what about smaller items? You cannot search everyone leaving the building, on the off chance that they might be pilfering company assets.
Would it not be nice if your assets were able to speak for themselves? Sounding a warning, for example, if moved to an inappropriate location, or surreptitiously removed from the building. Imagine if you could record every physical movement of every company asset, without a second's additional labour or paperwork. Asset tagging technology makes all this possible.
It is all on the label
Electronic asset tagging allows items of value to be fitted with a tag that indicates when normally static items (works of art, computer network servers, etc) are being moved or when portable items (laptop computers, etc) are being removed from a particular area or building. These systems are based on radio signal (RFID) transmissions. The tag will either transmit an alarm signal when it detects movement of a fixed asset, or if the tag on a portable asset is detected at the perimeter/exit of an area.
How does it work?
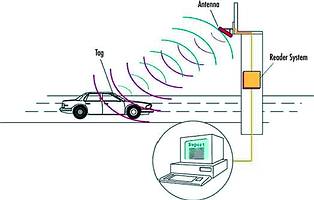
Asset tagging is based on a technology known as RFID (radio frequency identification). RFID is an information acquisition technology (much like bar codes, magnetic stripes or voice data entry), in that it provides an automatic way to collect information quickly, easily, and without human error. It is, however, rather more powerful, as it does not require contact or line of sight - and could, therefore, be used to identify an object inside a box or suitcase. RFID is also not sensitive to harsh dirty environments. It consists of a sensing device, which transmits a radio frequency signal to a specially designed tag, which then responds with another signal.
The process in detail
* A tag is attached to an object (such as a person, vehicle, laptop or asset), and encoded with identification information about the object in question.
* As the tagged object approaches an antenna, the antenna broadcasts a radio frequency signal toward it.
* The tag modifies the signal by adding its identification code, and reflects it back to the antenna.
* The antenna transmits the returning signal to the RF module, where it is preconditioned before being sent to the reader.
* The reader interprets the ID code from the signal and performs validation based on user-defined criteria. It can also append useful information (such as time and date) to the code.
* ID codes are then transmitted to a host computer or other data-logging device.
Potential applications
Asset tagging technology and RFID promises to deliver a host of exciting applications for the corporate market. Aside from attachment (as tags) to assets and objects, they can also be embedded into credit card size security badges, for contactless user identification. This type of monitoring would provide an additional level of security in high risk areas in case of any emergency evacuation.
Other applications include warehouse and storage, parcel and container tracking, stock control/inventory, airline baggage or passenger tagging and supply chain management.
The holistic approach
Asset tagging is simply another component of the holistic solutions available to companies who are serious about their security. Applied appropriately, asset tagging solutions (and accompanying reporting) become exponentially more powerful when integrated into a full system incorporating, for example, video surveillance, alarm management, access control and full reporting services.
Reference
1. Source: KPMG 2002 Global Information Security Survey.
For more information contact Jose Machado, Siemens Southern Africa, 011 652 2149, www.siemens.co.za
© Technews Publishing (Pty) Ltd. | All Rights Reserved.