

Every individual has the right to safety. Along with this, is the right to protect yourself effectively from harm, by any means, as long as those actions used may be justifiable and excusable by law.
This is all very well and good, but what needs to be taken into consideration in South Africa today is that the majority of criminals don’t care how much destruction they cause in order to get what they want, thus, even your life is considered worthless against the value of your cash, jewellery or cellphone.

The incidence of residential break-ins, with and without resultant violent assault, has grown to mammoth proportion in our nation and the police force cannot possibly cope with the influx of reported cases, let alone do pro-active and preventative policing. Thus, it is up to the individual to maintain a state of preparedness.
Despite shocking world-wide trends in the incidence of crime, many folks still have a very oblique view of what security is all about. Many families believe that putting in an alarm, with or without armed response, with a sign out front advertising the security installer involved, is enough
to prevent crime occurring at their address.
It is alarming how many people I have spoken to in the past who state that they have armed response, so if they do get broken into, they blame their security company or their nation’s public law-enforcement agency. However, what they are not taking into consideration is that both armed response and the police are both reactionary forces and cannot possibly be at all places, at all times.
Armed response companies and the police should be viewed as one leg of a family’s security plan, not the crutch on which our total security rests. The best security weapon we possess is our own mindset and in honing this weapon to concentrate on our vulnerability, we will be in a better position to counteract our security threats.
The propensity of many, in an attempt to ensure their family’s security, has been to purchase property within walled and security controlled complexes. However, this has also proven to be somewhat risky, as criminal syndicates can often afford to purchase property within these complexes and they literally prey on their complacent neighbours.
Trust is at a premium
We are living in a world where trust is at a premium and the only way to rest assured that we cover all our vulnerabilities, is to create a security plan for our homes and one can take stock of your vulnerabilities and rely on your armed response company or you can opt to have a professional risk assessment done. If one considers the security installers or armed response companies’ incentive to sell their services, it is possible that they might oversell. It is therefore advisable to have an independent risk assessment where the assessor is not directly involved with the actual installation of your security.
This is the reason as to why each household or business, whether in a complex or not, should invest in a security risk assessment.
There are a number of reasons as to why it is not advisable to create your own security plan without assistance. This becomes evident when we have a closer look at the steps generally followed in security planning, but needless to say, the untrained eye would fail to recognise all vulnerabilities and the untrained person would fail to employ the most effective countermeasures.
An independent security risk assessment helps to identify those areas in your home or property that are vulnerable to break-in or attack and should therefore be protected. The assessment also assists in the determination of which security controls need to be used and the type of security system that will best suit your needs.
Professor Bobby Ndungu from Zimbabwe designed a very comprehensive diagram, accurately portraying the circle of crime (Figure 1).
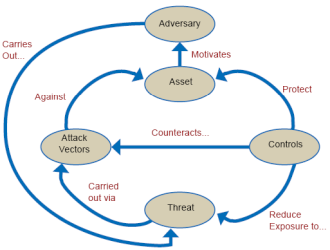
Let’s discuss the diagram in Figure 1 in detail. One owns an asset, this asset could be a valuable item such as a car, jewellery, electronic device or even, with human trafficking on the rise, a human being.
The desire to remove that asset from its current owner, motivates one’s adversary into carrying out a threat on that asset, using a variety of available attack vectors such as armed robbery, assault, house-breaking and theft etc.
However, the conscientious asset owner is advised to put in place certain security control measures, such as barriers, access control mechanisms, detective mechanisms and emergency response procedures, which have the ability to reduce the exposure to threat, counteract attack vectors and protect the assets.
Not all persons in South Africa can afford complex security equipment. However, by doing a complete security risk assessment and following a logical chain of thought, anyone can have a degree of protection.
A professional risk assessment will involve a ‘TRVA’, this stands for a Threat, Risk and Vulnerability Assessment. This assessment identifies what needs to be protected (assets, property or people), the nature of the threat to the assets, property or people, the risks which could exacerbate into events negatively affecting the asset, property or person and the vulnerabilities which allow these threats and risks to realise. What also needs to be kept in mind when doing a TRVA, however, are the constraints put on the eventual security solution, whether forced or voluntary, such as legal constraints, cultural constraints, operational constraints and especially budgetary constraints.
Independent advantages
The advantages of investing in a professional security assessor to carry out the TRVA for you, is that an experienced assessor enters your premises with a critical eye; a person who is not used to seeing the same landscape every day and thus will notice risks easier. Furthermore, he will have had prior experience with assessments and will know where to look for vulnerabilities and risks.
An assessor will look at all aspects of your security and not concentrate on only one aspect of protection. E.g. a camera installer will look at your premises with the intention of putting up cameras at all the vulnerable areas as this is how he generates his income; thus, you may find yourself subjected to one who tries to sell you as many cameras as he can get away with and sell you the most expensive product within his available range.
Having been in the risk assessment business for years myself, I have unfortunately come across some installers who are not to be trusted. Similarly, you may have the same propensity with guarding companies and barrier installers. The independent assessor will look at your premises like an onion, with various layers starting with the community around you and ending in the very core of your home.
Components of the TRVA
To determine threat, the assessor looks at the client’s property in conjunction with what is around it; open fields, highways, informal settlements, other residential complexes and free-standing properties. Not only do we have a look at those bordering the client’s property, but also those that are reasonably close to the property.
The reason these are considered a threat is that they provide either direct or indirect access to the property borders, yet also provide shelter to, or thoroughfare to potential perpetrators.
To determine the risk, it is necessary to look at the various statistics concerning crime and applicable criminal tendency for the immediate area in which the client’s property exists. In order to do this, the assessor will normally triangulate the client’s property in conjunction with the three nearest police stations. Taking these statistics into consideration, one can make the logical assumption that the crimes affecting one’s neighbours, by implication also affects the client.
Furthermore, the risk can also be determined by having verbal discussion with both the client and the client’s neighbours in terms of criminal activity that has taken place in the past; thus, retrospective risk is taken into consideration. What the assessor should remember is that not all criminal activity is reported to the police.
To determine vulnerability, the assessor looks at the physical security of the client’s property itself. Starting from access to the perimeter, as well as access control at the various entry and exit points on the property.
If the client or the client’s complex has a security guard on duty, then the assessor will attempt to penetrate the property by attempting to force the guard, bribe the guard or even bypass the guard whilst he is busy helping another client. This is to check that the guards uphold the standard expected of them by the client as well as the Private Security Industry Regulatory Authority (PSIRA). This exercise also gauges the honesty of the guards.
The assessor will then look at all potential entry points, taking into consideration the condition and integrity of the existing perimeter, the extra controls used supplementary to the initial perimeter, such as electrified fencing and barbed wire etc. and then test the integrity of these controls.
The assessor will evaluate the area of ground between the initial perimeter and the inner perimeter (the house itself) in order to determine whether there are hiding places for perpetrators, blind-spots or areas where security lighting fails to illuminate.
The next step is to look at the doors, security gates and burglar proofing on the building itself in order to check for vulnerabilities. It is one thing having barriers and security gates around your sensitive areas, such as bedrooms or lounges, but can your family escape a fire should one occur? Assessments must therefore evaluate your physical structure with the eye on maintaining a balance between safety and security.
It is then time for the assessor to attempt to penetrate and test the existing installed security equipment for integrity and quality. The assessor then tests the alarm, the CCTV cameras, as well as free standing security beams.
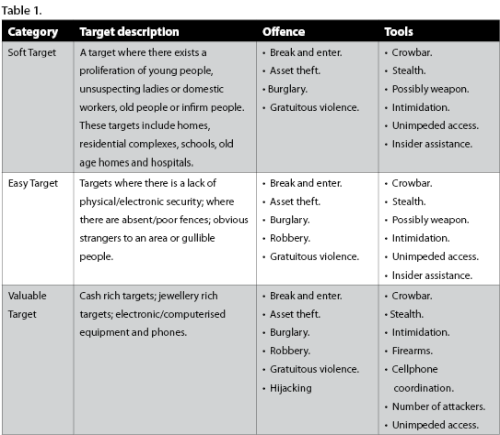
With all of the above done, the assessor is then in a position to categorise the client as in Table 1.
Violence is the order of the day
One also needs to keep in mind that violence has become the order of the day. The use of unprecedented violence has become so bad in this country, that the southern African region has the highest homicide and assault with grievous bodily harm rates in the world.
Most crimes in South Africa, especially crimes against homes and estates, are carried out with one or more of the following:
• Superior numbers.
• Superior firepower.
• Willingness to commit whatever violence necessary to achieve their goal.
• The use of fear, surprise and confusion.
The use of violence in South Africa is categorised as follows (courtesy of David Bruce – Centre for the Study of Violence and Reconciliation):
a. Instrumental violence:
The perpetrator uses violence for a practical purpose, such as:
• Self defence.
• Coercion (To force someone into co-operation).
• Making an example to scare others into co-operation.
b. Expressive Violence:
This form of violence is a means towards emotional satisfaction, including:
• Expression of anger or hatred.
• Satisfying the need for respect or control.
• Perpetrator gets satisfaction in hurting others.
c. Gratuitous violence:
This type of violence involves torture, mutilation or just plain ‘overkill’:
• It is heartless, callous and emotionless absolute cruelty.
• Can be due to Aggressive Sadistic Personality Disorder (ASPD).
• This person gets pleasure in the suffering of others.
• This is also the violence derived from racial hate or even gender issues.
• There seems to be no real reason for committing it other than the perpetrator wanted to at the time.
Summary of the security controls
Imagine if you will that your total security system takes the form of an onion. Onions, just as security, consist of layers and this is where your security controls find their value.
1. Preventative control
Preventative security controls can be divided into two layers. These layers include deterrence and access prevention. Most households already have these in place to a lesser or greater degree as most homes have a perimeter fence or wall, burglar bars, security gates (access prevention) and many have a dog or two (deterrence). Just a note on deterrence, the advertising board of your security or armed reaction company will not deter the would be assailant from entering your premises as they have, in many cases, done their homework on these companies and often know where their vehicles respond from and what the average response time is.
By adding barbed/razor wire, spikes or electrified fencing to the top of your wall or fence, you are increasing your preventative controls as they often act as both deterrents as well as prevent access to an extent.
Secondly, because we know that no wall, fence or security gate is totally impregnable, we need to have our second control in place.
2. Detective control
Detective controls identify that something is amiss and alarm us of this abnormality. Detective controls can take many forms, but to give a few common examples we look at CCTV cameras either linked to a digital video recorder or linked to a monitor which give a push notification to your phone or alarm when they pick up abnormality, movement sensors connected to an alarm, lights connected to movement sensors. Other common detective controls also include dogs or a very vigilant neighbourhood watch.
3. Corrective control.
Corrective controls are those controls designed to lessen the damage when the preventative controls have been breached and the detective controls have reported that breach. Corrective controls include examples such as armed response, neighbour response and self-defence, either armed or unarmed.
In conclusion
With violence in mind, security becomes less of a grudge purchase and more of a desirable state of mind. People want to be assured that their families are safe and that their physical property is not damaged or stolen. Furthermore, each of us needs to be able to sleep at night or go away on holiday without anxiously thinking about the vulnerability of our security.
A security risk assessor can make the necessary informed recommendations, taking into account the client’s budget, proclivities, as well as the type or size of the garden, house or complex and the type of security equipment needed to cover all the vulnerabilities. This is done whilst preserving the aesthetic value of the property.
The assessor’s job does not end when the assessment is finalised. After the installations have taken place according to the recommendations, it is valuable to re-assess the risks and confirm if the controls have been put in place and if there was indeed an improvement in terms of security vulnerability.
In the end, if the client and the assessor can agree that the measures in place deter, deny, detect or delay the commission of a crime and assist the client to respond effectively to and recover from untoward events, then the small cost in hiring an assessor becomes worth it.
Homeowners and homeowner associations should also keep in mind that circumstances change around them all the time: political changes, new forms of crime and violence, new security products on the market etc. All of these change one’s security landscape. Thus, it is necessary to get an assessment every few years, in order to stay current.
Another plus point to remember, when determining the return on investment in terms of a security assessment, is that, should one carry out the assessor’s recommendations partially or in full, one becomes less of a risk to the insurance company, thus, one is able to insist on a lower premium. In some cases, this will cover the cost of the assessment within the first two months.
For more information, contact Andy Lawler, Sentinel Risk Management, +27 82 953 1594, [email protected], www.sentinelriskmanagement.com
© Technews Publishing (Pty) Ltd. | All Rights Reserved.