
With more and more corporations and organisations owning multiple sites in various countries around the world, with capital equipment becoming smaller in size, as well as mobile, and with employees needing the freedom to freely move around in this environment, being able to monitor assets location and status in the workplace, in realtime, has become a major requirement.
An example of this need for mobility is in hospitals, which no longer require patients to be taken to the equipment room, the mobile X-ray machine is now taken to the patient. Another example is the horrendous amount of laptop computers that are stolen every year, and which contain vital company intellectual property. With the latest developments in long-range RFID and infra-red (IR) communication, a solution is no longer a fantasy of some technology geek, given that a new class of cost-effective enterprise local positioning applications and systems are being implemented successfully all over the world.
The next few suggestions are essential requirements to look for in an enterprise local positioning system (LPS), when evaluating the purchase of such a system.
The first question to ask is what type of LPS solutions would benefit your organisation and how this is going to influence your LPS requirements? Before conducting this survey, it is recommended to study the different kinds of solutions on offer from vendors, as well as the solutions they are aiming to achieve in the future.
Relevant points include:
1. Will I need a room resolution, a general area resolution, or even exit resolution
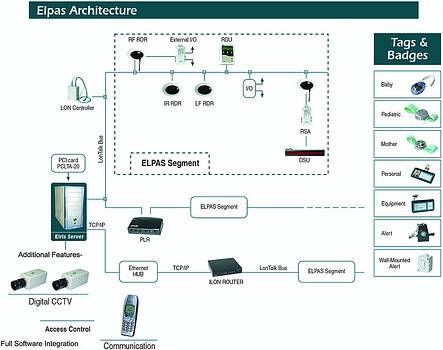
For the computer location you might settle for a general area, but if you expect the system to notify of laptop computers being illegally removed, you will need a door resolution. Hospitals that want to automate their nurse call system will need to know the exact nurse room location. Soon after looking into the different requirements you come to the conclusion that even if you want to start with an area resolution solution, you nevertheless want to ensure that the chosen system will offer the flexibility to improve the resolution in a cost- effective manner. Due to the limitations of each individual medium, the most cost-effective way to achieve the above is to have a system that uses the same infrastructure to support a transmission of low and high RF as well as IR (IRFID technology).
2. Variety of tags. As you implement the system throughout the enterprise you will discover that you need a variety of IRFID tags from both a design and functionality perspective. You should ensure that the system you choose includes the correct tags to address your different needs. The following is a list of several examples:
* An equipment tag that should be tiny in size and provide tampering indication.
* An employee tag which includes the employee's picture and the company's logo.
* A tag used in cases of an attack with an easy-to-use button press.
* A baby tag that should be small in size and provide a tampering alarm.
Bear in mind that the more features these tags offer, the more solutions can be applied to the same infrastructure, thereby improving return on investment.
3. Smart RDRs. Conventional systems use sensors to provide input to a 'brain' that calculates location only. However, as the world moves increasingly towards a distributed intelligence approach, you may decide upon a more advanced system that uses RDRs with distributed intelligence to provide scalability of functions from which you can choose input and output relays that are activated locally by the RDR. This improves reliability and speed reaction.
4. Will location be good enough for me or can I expect to receive more to justify my investment? While conventional systems provide information based on the three Ws, I strongly recommend demanding the fourth W as described below:
* Who is wearing the tag/badge? (Thus, the identification of the person or equipment.)
* When - to constantly monitor and provide realtime and history log?
* Where was the tag last detected?
* What is the status of the equipment piece to which the tag is attached?
This can include information such as: Is the equipment plugged in to an electrical outlet?
If it is plugged in, is it currently in use? If it is in use, what is the equipment's utilisation level (remaining battery level, oxygen level used, temperature and more)?
5. An open standard network architecture should be applied. A good example of such a network is the Echelon LonWorks network, which has an easy 'plug & drop' concept, providing the following three benefits:
* Enables adding components from a variety of other systems, such as access control and energy management, on the same network. There are currently about 3500 LonWorks-compatible components available, thus providing complete building control and management solutions.
* Seamless conversion to TCP/IP: Numerous buildings within the site or around the world can operate on one system, using the existing computer network TCP/IP infrastructure. For example, a hospital site that has a TCP/IP infrastructure within its building enables the security office to remotely activate doors, alarms etc, using the existing infrastructure.
* With today's constantly changing environments, flexibility in design plays a major role in reducing the cost to install, expand or modify the network (plug and drop) thereby reducing the cost of ownership.
Flexible software architecture: a local positioning system should be flexible enough to offer the following capabilities:
* Software development kit (SDK) in commonly-used formats, such as COM and C++, to allow for easy and rapid customisation and development of applications to meet the needs of evolving organisations.
* Selection capability of the appropriate type of database, depending on the size and the needs of the organisation (from Microsoft Access database for small organisations, up to Microsoft SQL for robust database needs). Regardless of the type of database selected, its installation and basic configuration should be embedded in the local positioning system's installation.
In conclusion, if one wanted to combine all the above suggestions into two words, it would be worth remembering that in this fast-moving, fast-changing and complex business-world, a powerful local positioning system must be flexible in its design and in the amount of applications that it can offer. It should be completely open from the component level to the network level and all the way up to the application level. These two guiding principles ensure that you receive better return on your assets as well as on the system itself and increases your chances of meeting the demands of any organisation not only today, but also in the future.
© Technews Publishing (Pty) Ltd. | All Rights Reserved.