
The trouble with thinking about technology advancements is that the rate of past progress does not predict the rate of future progress. Prices go down, while capabilities go up – but not at an even rate of progress. It’s a continual acceleration of the rate of progress.
It is a little known, but provable fact that all information technology advances follow the same type of growth curve. It starts out slow, begins to build, and then takes off like a rocket.
A number of individuals have closely examined these technology trends. Chief among them is Ray Kurzweil, a highly accomplished inventor, futurist and author. Kurzweil was the principal inventor of the first CCD flatbed scanner, the first omni-font optical character recognition, the first print-to-speech reading machine for the blind, the first text-to-speech synthesiser, the first music synthesiser capable of recreating the grand piano and other orchestral instruments, and the first commercially marketed large-vocabulary speech recognition. In 2012, Kurzweil became the director of engineering at Google, heading up a team developing machine intelligence and natural language understanding (i.e. applications you can talk to in a conversational way).
About technology advancement, Kurzweil says, “. . . if a technology is an information technology, the basic measures of price/performance and capacity (per unit of time or cost, or other resource) follow amazingly precise exponential trajectories.”
For example, Martin Cooper, an American engineer who is considered to be the 'father of the cellphone', discovered that the amount of information that can be transmitted over a given amount of radio spectrum has been doubling every 2.5 years since Marconi’s first radio transmissions in 1895. This fact is known as Cooper’s Law.
Additional technology 'laws', which are really observations, are:
• Moore’s Law: “Processing powers doubles about every two years while prices are halved.”
• Gilder’s Law: “Network bandwidth doubles every six months.”
• Less’s Law: “The cost of storage is falling by half every 12 months, while capacity doubles.”
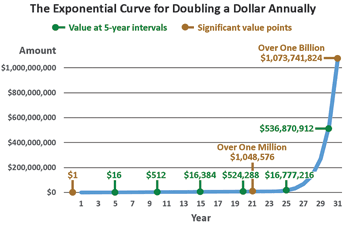
An information technology’s growth will double at some specific rate, typically ranging from annually to every five years. What is important to note is that regardless of how fast the doubling occurs, the shape of the trend curve is essentially identical from technology to technology. The classic shape of such a trend curve, known as an exponential curve, is clearly visible in Figure 1, which tracks the growth of money value for a hypothetical bank account whose balance begins at $1, and doubles every year.
These trends apply to all information technologies. While the success or failure of any particular company or product is not predictable, the rate of advancement for a particular information technology is definitely very predictable.
This is what makes it possible to predict the rate of advancement for physical security systems technology. There is a natural security industry technology adoption lag – it’s the time it takes for manufacturers to understand new technology, identify its security uses and incorporate the technology in their product lines. By keeping an eye on the IT trends, it’s possible to see the advances coming well before they appear as new or upgraded security products.
Figure 1 provides an example of the kind of growth curve that characterises information technology advancement, except the graph is about dollars, as money is a quantifiable thing that helps illustrate the magnitude of the advancement that is about to take place for security technology. In an exponential graph, initially, progress is very slow. In this example graph, in the first 10 years the amount has grown from $1 to $512. In the second 10 years, it grows by more than $500 000. But in the following 11 years, the account balance surpasses $1 billion.
The Figure 1 graph illustrates an important point about exponential trends: at no time in the trend line does the previous 5 or 10 years of growth give a clear indication of the next 5 or 10 years’ worth of growth, unless one already knew that the growth rate is exponential. It’s the same with information technology advances. The larger progression of this accelerating growth curve is not intuitive. One of the reasons is that when we humans experience this type of technology trend, we tend to project the future based upon the recent growth experience (the last five or 10 years) rather than the actual exponential growth curve coming up.
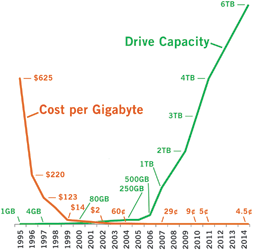
Figure 2 is a good example of information technology’s price/performance and capacity curves. It depicts the drive capacity and cost per Gigabyte trends of computer hard drives. The graph shows how the common pace of technology advancement increases at an ever-accelerating rate, starting out slowly and then ramping up dramatically. Typically, the cost trends are almost the mirror opposite of the capabilities trend, dropping steeply at first, and then levelling out.
100 years of advancement in less than a decade
Because electronic physical security systems are based on information technology, physical security systems will follow the same advancement curve of information technologies. The pace will explode from its current state at an accelerated pace to include security operations not even yet considered. While most security professionals believe technology convergence has already happened for the security industry – in truth it has barely begun.
That steep upward climb on the right-hand side of the technology advancement curve represents what happens when convergence starts to take hold and industries embrace information technology advancement trends (computing, networking, software, analytics, miniaturisation, virtualisation, consumerisation, etc.). If companies embrace only the recent advancements and not the actual trends, they fall behind. That’s been the state of things in the security industry for the past decade – well behind the curve of IT advancement. An industry’s companies have to embrace the trends themselves, and become a part of those trends. That’s how industry-specific technology advances.
This has already been happening, for example, in the automotive industry, an industry where the Society of Automotive Engineers (SAE) has been holding semi-annual convergence conferences for over 30 years. One of the high-interest panel discussions at SAE 2014 Convergence was titled, '40-Year Look Ahead'. Why do they look that far ahead? One reason is that the increasingly rapid pace of technology advancement will shrink that 40-year period by at least half.
15 years ago, who thought we’d have self-parking cars? Hardly anyone, except the forward thinking people at the SAE Convergence conference. Who thought that driverless vehicles would be piloted by a search engine company (Google) and a bookseller (Amazon)? Obviously Google and Amazon have redefined themselves to include much more than just Internet searching and selling books online. This is another aspect of convergence and consumerisation trends – cross-industry collaboration and innovation.
It’s hard for people to envision a pace of technology advancement that is 10 times faster than it is today. That’s why the forward look has to stretch into futuristic thinking, because the future is almost here.
The position of the security industry
It is important to realise that most information technologies have already rounded the corner of their technology advancement curve and are on their way to extremely high rates of advancement, as can be seen in Figure 3. Security technology will advance through the up-swinging curve, and in the next 10 years it will seem like more than 100 years of progress is taking place compared to the previous 10 years. The pace of advancement will pick up slowly, round the speed corner, and after that take off like a rocket.
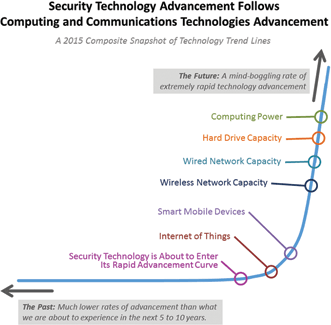
It is hard to envision this much advancement now, partly because of the constraints that handcuff the security industry. Yet the visionaries will have to look past these constraints, as technology advancement is set to eliminate them in short order. Security technology companies that limit their designs based on current constraints will in essence be designing obsolete products and services.
Individual illustrations of the growth trends of the technologies depicted in Figure 3 are available online at: www.go-rbcs.com/tech-growth-curves
Two constraints changing: Internet bandwidth and security
The Internet bandwidth constraint is already eroding, as evidenced by home networking speeds that are now 60 times what they were 10 years ago (and 120 times what they were 15 years ago), and 10 years from now will be 60 times what they are now. Nielsen’s Law of Internet Bandwidth states that a high-end user’s connection speed grows by 50% per year. That law fits data from 1983 to 2014.
A number of initiatives are working to secure the Internet, the most notable being the Electronic Frontier Foundation’s project to encrypt the entire Internet. Mid-year 2015, they are launching a security certificate authority (organisation that issues the digital certificates used to make secure Internet connections) named Let’s Encrypt (http://bit.ly/lets-encrypt), whose purpose is to secure the entire Internet by automating Web security and making it free.
This effort, led by the Electronic Frontier Foundation, includes Mozilla, Cisco, Akamai, IdenTrust and researchers at the University of Michigan. This initiative only secures the Internet connections themselves. It does not secure the Web applications, but application security has its own trend of advancement and these trends will all combine to drastically reduce the risk involved with Internet transactions.
As the Internet bandwidth constraint lifts, and security for Web services drastically improves, suddenly cloud-based security services start making a lot more sense. Cloud-based services are poised to be as big a part of the security services landscape as are other service-based applications for other business sectors.
Changes coming to the security industry
What changes will take place within the security industry? We can look to Silicon Valley both for examples of what to do, and also what not to do. These insights will encourage security industry companies and help them to make moves that they previously would not have considered.
A lot of Internet and Web innovation came from small companies that developed breakthrough technologies of one kind or another, and then got acquired by Cisco, Yahoo!, Google, Amazon and many other companies whose names we all know. At one point a while back, over a period of several months, Cisco was acquiring five or six companies per week. Technology advancement creates opportunities that many bright young people will embrace, and this will feed new life into traditional security companies that are not yet able to move at the fast pace that is required.
Technology advancement and your security programme
Just 20 years ago, physical security technology had significant limitations. The process of deploying security technology involved compromise with security operation’s objectives, usually due to high costs or to shortcomings in what the technology could do. However, today the two overall information technology trends – increasing capabilities and decreasing prices – mean that if you can’t already do everything that you want to do with your security systems deployments, you’ll be able to very soon. And it won’t be long before you will be able to put Star Trek-like command and control capabilities to work for you.
However, most security departments are not prepared for advanced technology – and the state of their current technology practices is at least a decade behind the successful practices of IT.
For many security departments, to embrace the coming technology wave requires transitioning from the old-school technology thinking that grew around standalone and closed-network systems, to current-day thinking that includes the successful practices of IT. After all, the IT domain has been part of information technology advancement for more than a decade. Security departments must begin to treat technology the way that IT is already doing.
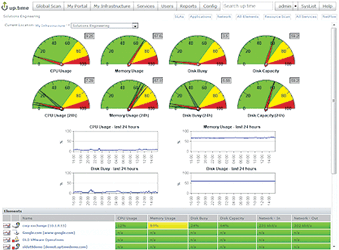
IT uses software tools to perform around-the-clock monitoring of IT infrastructure and alert the appropriate parties when any infrastructure conditions depart from their normal parameters, which allows them to detect early warning signs, and at the very least to detect and immediately respond to any problem.
Figures 4 and 5 depict the difference between the IT approach to monitoring IT infrastructure and the infrastructure monitoring situation for most security departments. In fact, most security departments don’t know that IT-style technology for monitoring video infrastructure exists right now, and can be easily found by performing an Internet search for 'Video Path Uptime'.

Seven steps you can take to start getting ready
A future article will elaborate on the bullet points below. Carry out these actions in whatever order makes the most sense for your organisation.
One: Get your security system documentation current.
Things move fast in the IT world, and one of the reasons they can move quickly and effectively is the attention paid to systems documentation.
Two: Update your facility risk assessments.
This refers to an honest-to-gosh formal assessment where critical assets and their threats and vulnerabilities are identified, the likelihood of incidents is worked out along with potential business impacts. The result should be a risk treatment plan that brings the security risks down to acceptable levels at an acceptable cost.
Three: Develop a Security Concept of Operations
A Security Concept of Operations document establishes the context within which security technology will support security operations. (See: http://bit.ly/security-conops)
Four: Understand IT’s technology roadmap and managed infrastructure
Have someone in IT explain their technology roadmap to you, or read the document yourself if you are up to the task. Learn what it means to have an infrastructure that is managed in real time.
Five: Join your local ASIS chapter if you are not already a member
As a chapter member, you can influence the topics selected for lunch presentations, and include emerging technology in the list.
Six: Check out the ASIS Member Councils and their newsletters
ASIS has launched a new member council that actively keeps an eye on emerging technologies, called the Security Applied Sciences Council (SASC, https://www.asisonline.org/Membership/Member-Center/Councils/Security-Applied-Sciences-Ad-Hoc-Council/Pages/default.aspx). The SASC will be monitoring security technology developments and actively engaging with security professionals who are end-users, engineers, vendors, testers, and subject matter experts in the field of security technology applied sciences. The Physical Security Council (PSC) offers workshops on several security technology topics, and other business sector councils offer workshops specific to security for banking, healthcare, pharmaceutical manufacturing, and other facilities. The PSC’s website has some excellent downloadable resources.
Seven: Start a written technology wish list
In whatever document format suits you, create a wish list for future security technology that will hold all of your ideas for what you would like your next generation of security technology to do for you. Date your entries. There are two categories of security improvements: security-effectiveness and cost-effectiveness. Identify which category each wish-list item is in.
Getting current with existing technology
Getting current with your existing security systems deployment is a solid step in preparing for the coming technology changes. While performing the steps above, you will become aware of any technology shortcomings, get a sound idea of the current state of things, and probably have some good thoughts regarding how you want to evolve your security technology capabilities.
© Technews Publishing (Pty) Ltd. | All Rights Reserved.